Secrets
Secrets in the context of APIs often refer to sensitive data that your application needs to function but which you don’t want to be openly accessible.
This could be API keys, database credentials, JWT secrets, and so on. It’s crucial to handle these secrets securely to prevent unauthorized access and potential security breaches. This section will guide you through the best practices for managing and using secrets in your APIs.
Important
Never store secrets in your source code, version control or in plain text in app. This is a common mistake that can lead to serious security issues. Instead, use our secure secrets management system.
Secrets Management
In order to access and manage secrets, navigate to Secrets page from left menu:
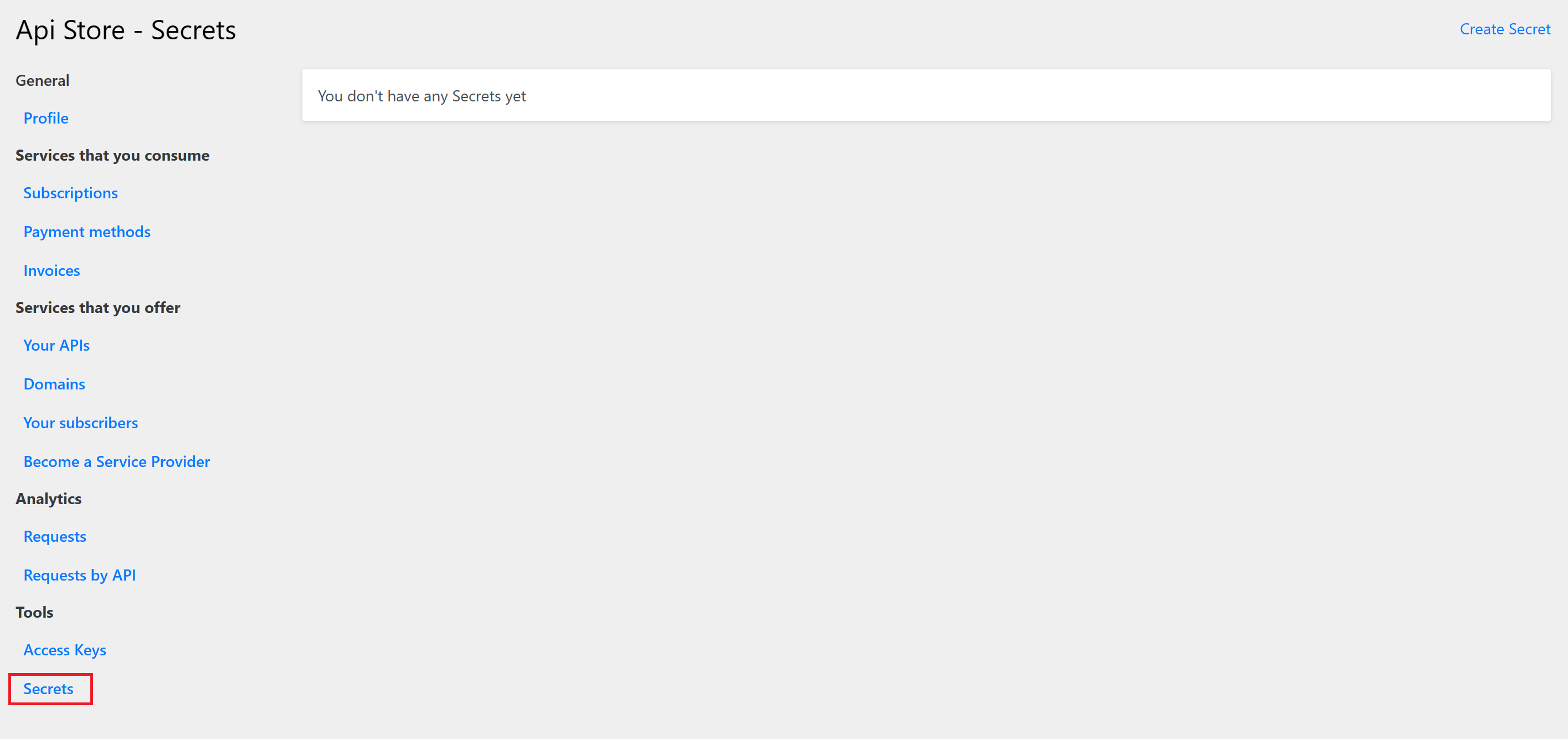
CLick on Create Secret:
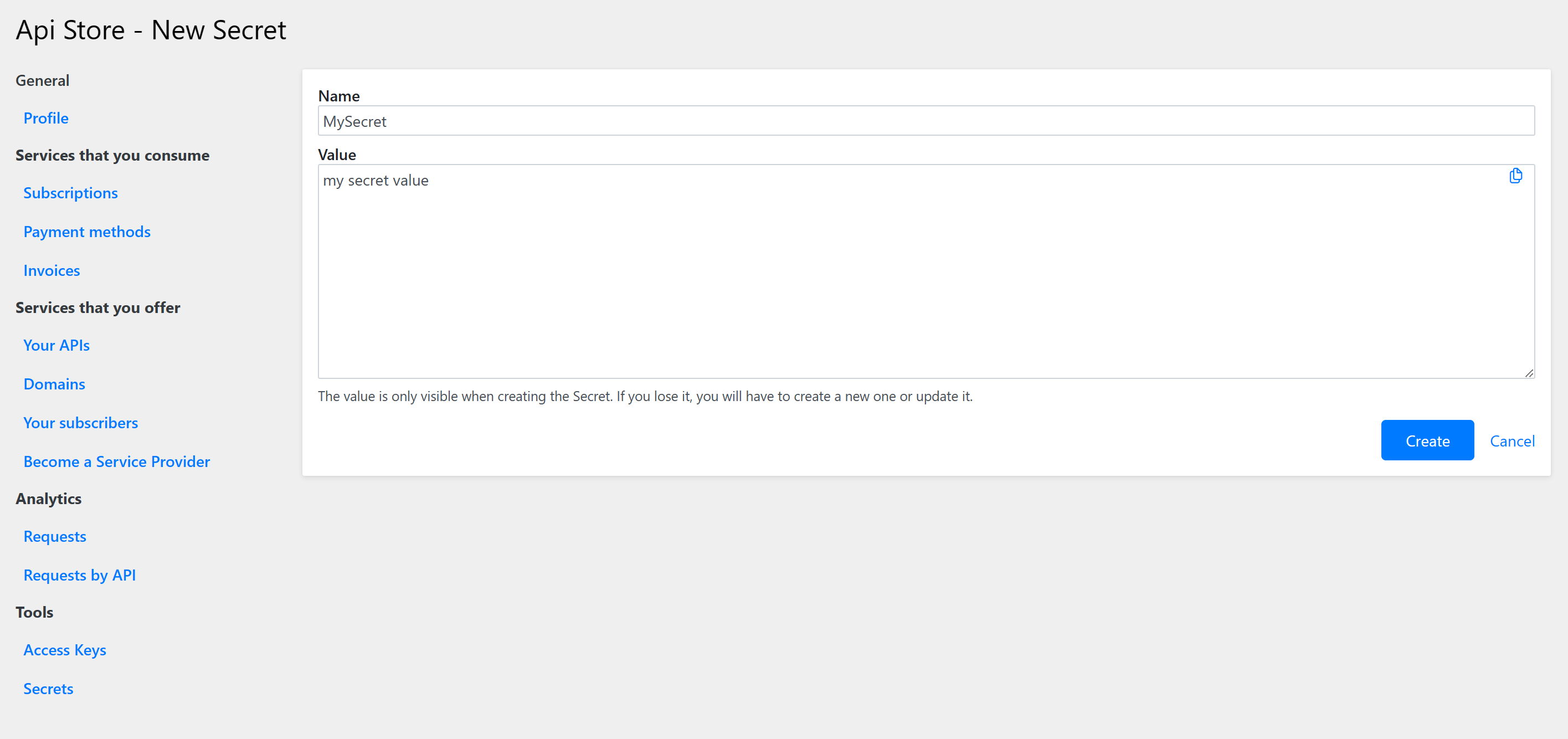
Enter a unique name, the value and click Create.
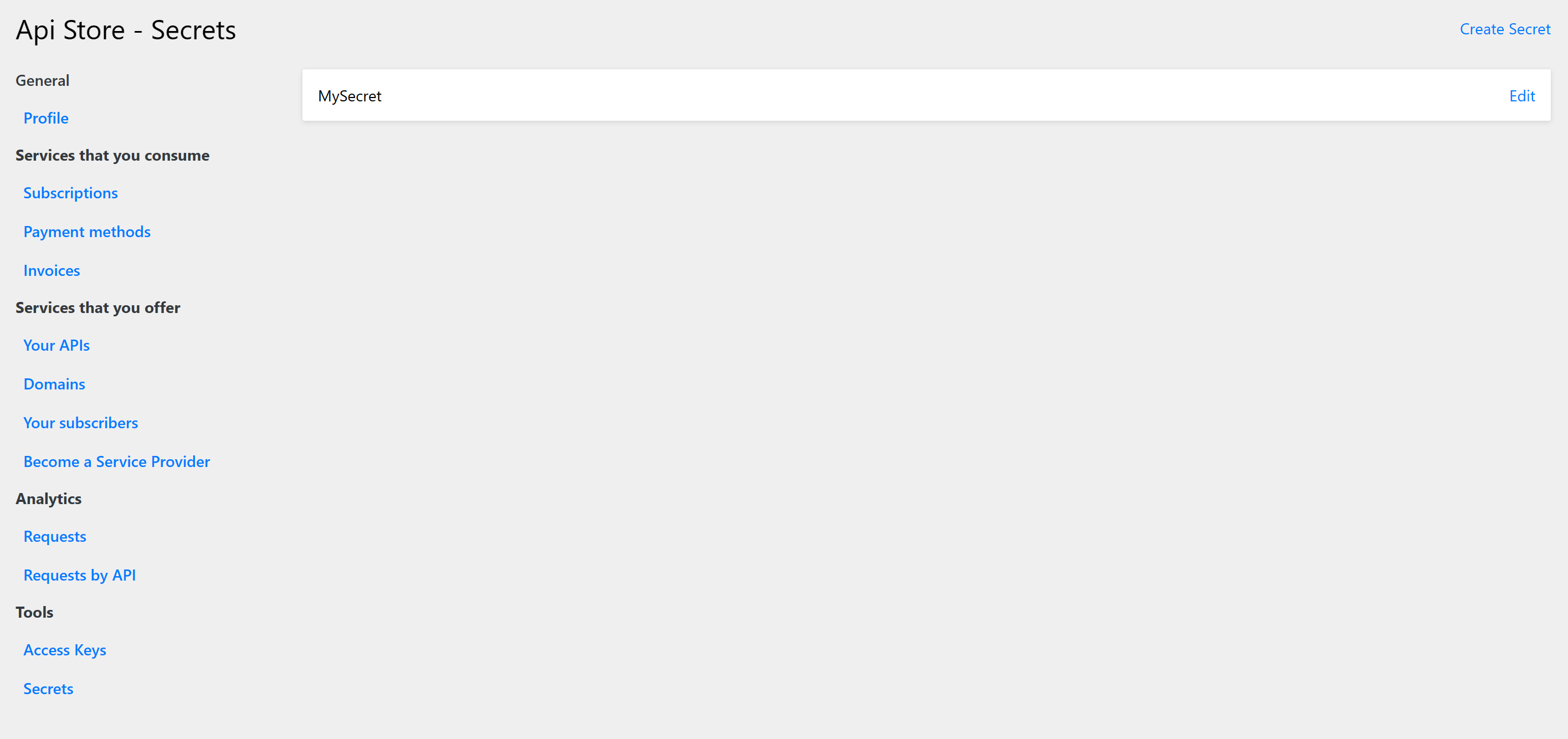
Your Secret is now securely stored:
Using Secrets
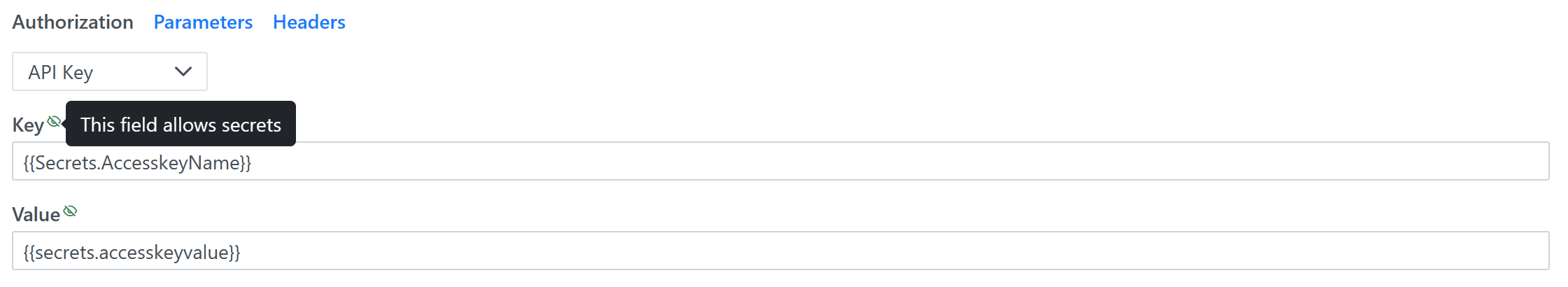
This secret can be utilized throughout application by referencing it as follows: {{Secrets.MySecret}}. The name is case insensitive, so the {{secrets.mysecret}} value will also work. The fields that allow secrets have a small icon in their label:
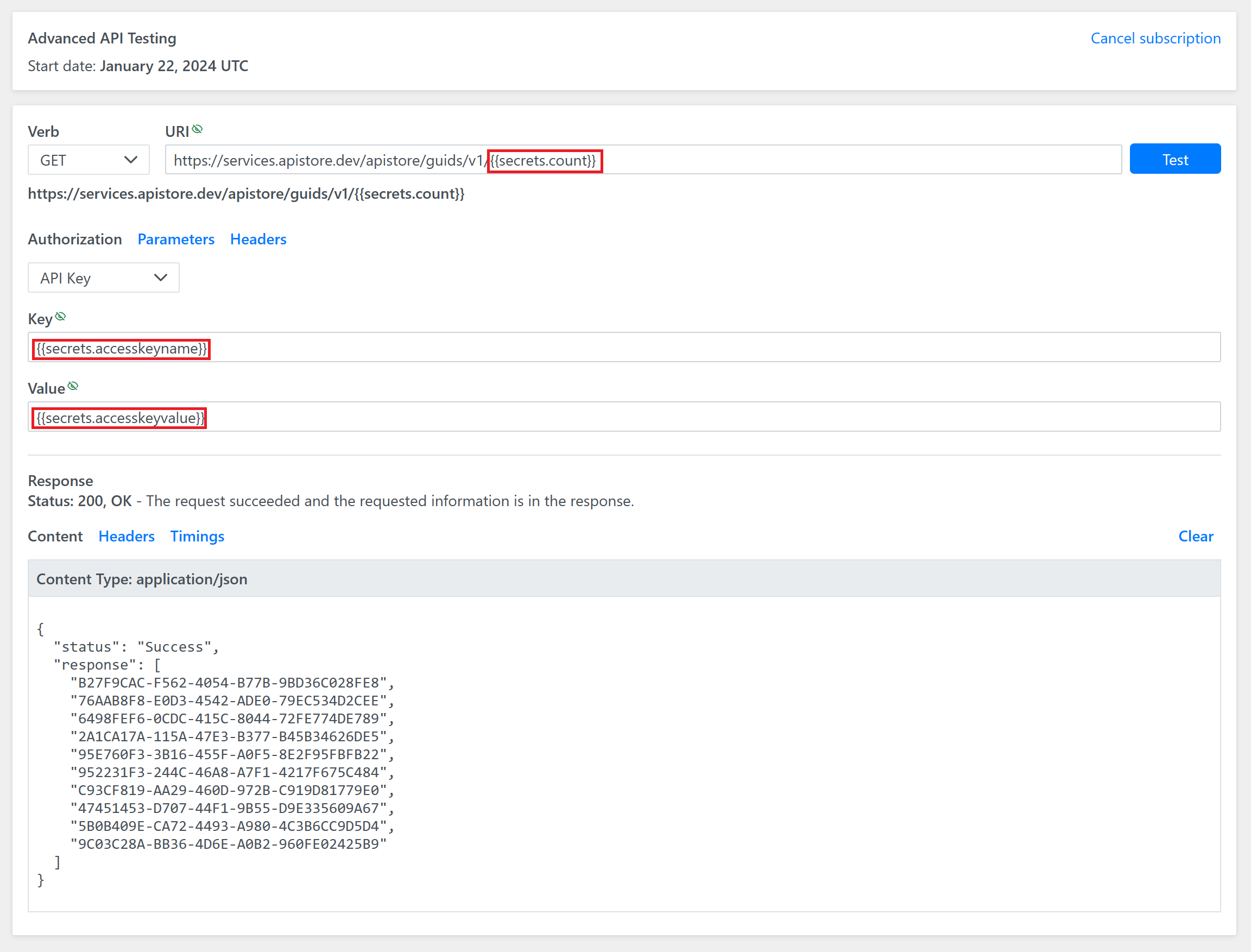
Below is a screenshot that demonstrates how you can use the secrets in Api Store fields:
Important
The secret value is only visible at the time of creation. After that, it's securely stored and not directly accessible. This means that if you forget a secret or lose access to it, you'll need to create a new one.
Secret Leaks
Despite your best efforts, there may be situations where a secret is accidentally committed to a version control system or leaked in some other way. If you suspect that a secret has been leaked, you should rotate it immediately. This means creating a new secret and replacing the old one wherever it's used.
In addition, you should investigate the leak to understand how it happened and take steps to prevent it from happening again. This could involve changing your processes, improving your tooling, or providing additional training to your team.
